Bitdefender Threat Debrief | April 2024

We're excited to unveil the next chapter of Bitdefender Threat Debrief. Since 2021, we've been keeping the cybersecurity community informed about the evolving threat landscape through monthly reports on ransomware, phishing, honeypots, and Android trojans. This issue introduces a significant shift in data collection: ransomware reports will now leverage victim data directly from attacker websites. This replaces our prior reliance on detection data, offering a more comprehensive view of the threat landscape. Starting with this edition, we're bringing you the latest and newest ransomware news in each segment – it’s crucial intel every security expert should be on top of to stay ahead of threats.
This month reveals a disturbing tactic: new ransomware groups are attempting to poach disgruntled affiliates from groups like BlackCat (who recently pulled an exit scam). These affiliates, who may possess stolen data from previous attacks – data the victims already paid for – could be lured into a second extortion attempt, reopening old wounds for these companies. This gives a completely new meaning to “double-extortion”.
Ransomware Report
Staying ahead of ransomware attackers is a constant battle for security specialists. By monitoring trends in victim data, attack methods, and targeted industries, we can gain valuable insights into the evolving tactics of these cybercriminals.
Top 10 Ransomware Groups
The Threat Debrief leverages data directly from ransomware group websites, primarily focusing on their claimed victim counts. This approach offers valuable insights into the RaaS market's activity level by reflecting attackers' self-reported successes. However, it's crucial to acknowledge the inherent limitations. We are relying on information from criminals, and their claims may be inflated or fabricated. Additionally, this methodology only captures the number of claimed victims, not the actual ransom demands or payments made.
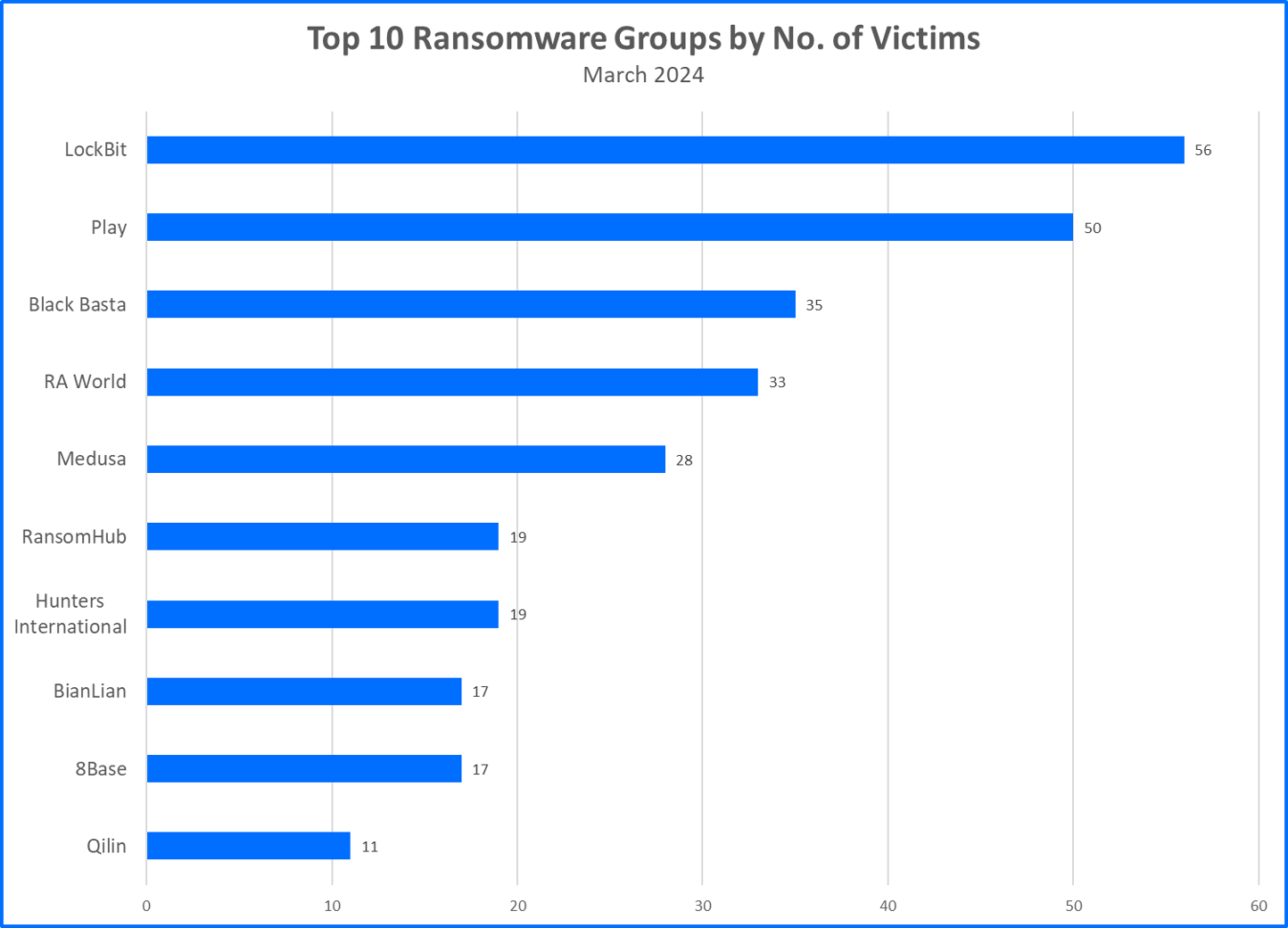
Now, let’s explore the most notable ransomware news and findings since our last Threat Debrief release:
- BlackCat (ALPHV) Stages Exit Scam: The BlackCat ransomware collective seemingly orchestrated an elaborate exit scam, shutting down their storefront and replacing it with a fabricated law enforcement seizure notice. Security researchers quickly exposed the charade, highlighting the ever-present distrust within the RaaS ecosystem.
- LockBit Develops Next Iteration: LockBit, retaining the top spot by claimed victims (56), is reportedly working on LockBit-NG-Dev (likely v4.0). This new version is moving away from the traditional C/C++ programming languages and towards the .NET framework. LockBit-NG-Dev is compiled with CoreRT, which could allow LockBit to run their malware on other operating systems like Linux, macOS, and even mobile devices. This new sample is packed with MPRESS for further obfuscation, making it potentially harder to identify.
- Play Ransomware Hits Government Contractor: A Play ransomware attack breached Xplain, a government contractor in Switzerland. The attack exposed roughly 65,000 sensitive federal documents, primarily impacting the justice and police department with leaked personal data, classified information, and passwords. This incident underlines the vulnerability of government supply chains to ransomware attacks.
- RA World Expands Globally: Previously focused on South Korea and the US, RA World is now a global threat. This month, they rank fourth with 33 claimed victims, showcasing their expansion into Europe (most victims in Germany and UK), Asia (India, Taiwan, South Korea…) or Latin America (Mexico).
- RaaS Bidding War Heats Up: In a battle for talent, RaaS startups are offering lucrative deals. Medusa, a midmarket group, targets former ALPHV and LockBit affiliates with a revenue share model starting at 70/30 and skyrocketing to 90/10 for million-dollar ransoms. They also provide 24/7 support, aiming to be a one-stop shop for affiliates.
- RansomHub: Trust Us, We're Ransomware: Rising quickly, RansomHub offers a generous 90/10 split and allows collaboration with other groups. Interestingly, they claim a code of conduct, refusing to target non-profits and specific countries including the Commonwealth of Independent States (alliance of some ex-Soviet states), Cuba, North Korea, and China. However, public pronouncements in the ransomware world are often unreliable.
Top 10 Countries
Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. This often means focusing on developed countries. In March 2024, we analyzed data from ransomware group websites, identifying a total of 346 claimed victims. Now, let’s see the top 10 countries that took the biggest hit from these attacks.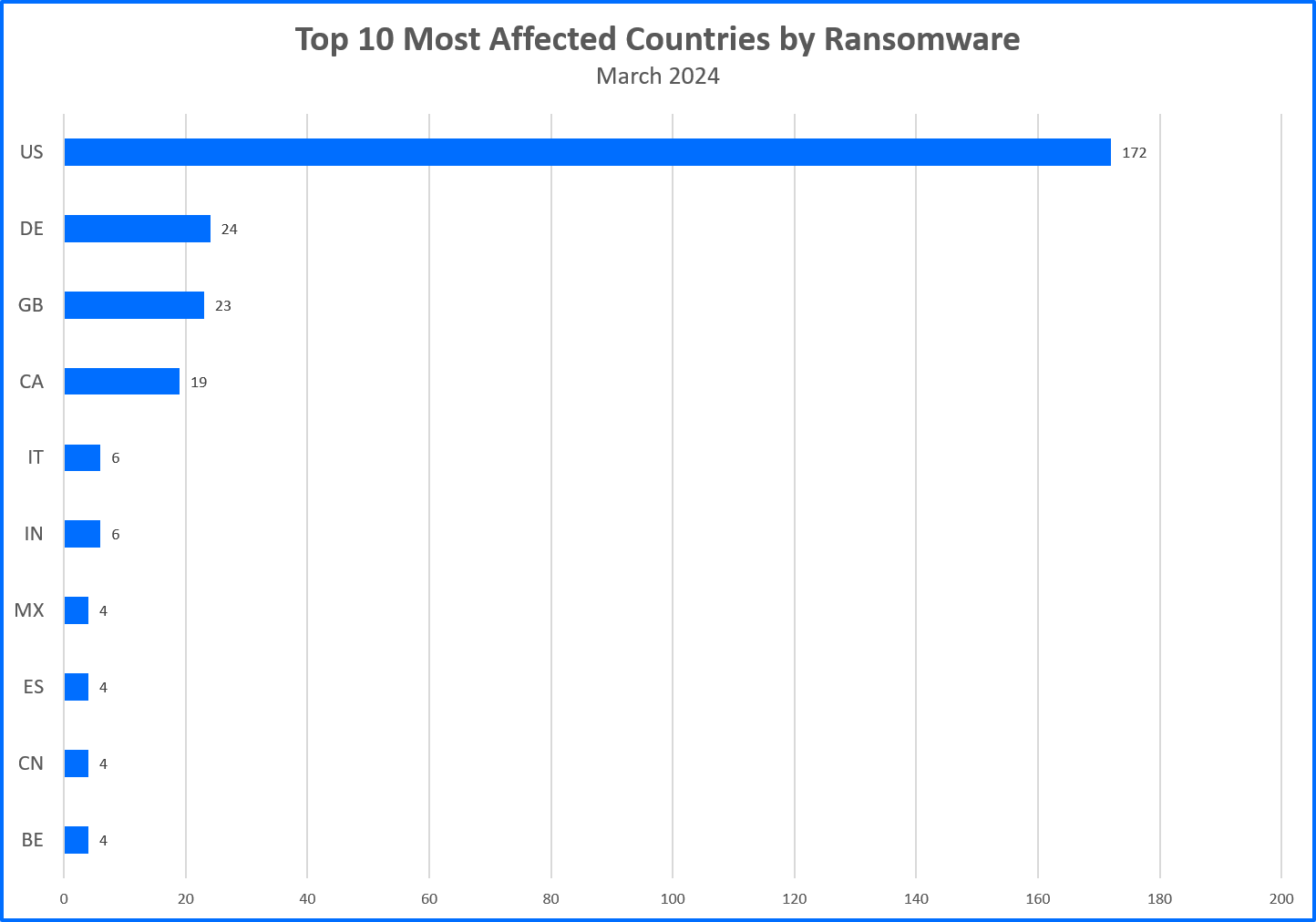
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on Twitter. You can find all previous debriefs here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 180 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank Bitdefenders Alin Damian, Mihai Leonte, Andrei Mogage, Silviu Sofronie, Rares Radu, Ioan Stan, Marius Tivadar, and Horia Zegheru (sorted alphabetically) for their help with putting this report together.
tags
Author

Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks






